BabaYaga is the moniker of a new strain of WordPress malware that has been making a name for itself lately. It’s unusual because it is actually capable of removing other malware in order to easier infect your site. However, this doesn’t mean it’s friendly, or that it can’t do damage to your site.
In this article, we’re going to tell you everything you need to know about this new threat. We’ll be discussing how you can be affected by the BabaYaga malware, and provide you with recommendations to keep your site clean.
Let’s go!
Introducing the BabaYaga Malware
BabaYaga was recently introduced to the world thanks to a comprehensive report from Wordfence. According to the initial report, BabaYaga isn’t actually a new threat. However, it caught the attention of the team due to its unusually comprehensive methods for infecting sites:
None of these countermeasures are groundbreaking individually, but taken as a whole they comprise a suite of functionality unusually comprehensive and effective for spam droppers.
BabaYaga is also noteworthy in that it only targets WordPress sites. As such, it’s particularly resilient against many of the standard ways of detecting and removing malware. We’ve already discussed in previous articles about how WordPress malware is a serious problem, so you should always keep yourself up-to-date with the latest security threats. As such, let’s look a little closer at BabaYaga.
What BabaYaga Does to Your WordPress Site
The most prominent feature of the BabaYaga malware is its ability to get rid of its ‘competitors’. In short, BabaYaga eats other malware. While this may make it sound great, like having a friendly spider eating the flies in your house, it’s actually more insidious.
The reason BabaYaga gets rid of other malware is to keep itself hidden. As the white paper published by Wordfence says:
A good parasite wants to keep its host alive. If everything is up and working properly, the owner of an affected site can go without knowing anything is wrong indefinitely.
Essentially, if malware makes its own existence obvious, the owner of the site is likely to scrub their site of allmalicious programs. BabaYaga therefore silently removes these other threats so you won’t notice it’s there.
However, what does it actually do? Once BabaYaga has infected your site, it will begin to generate spam content. The generated pages will be full of keyword stuffing, which will obviously show up in search engines. If someone were to click a link, they’d be taken to an external affiliate site. Essentially, it’s a way to use your site to drive dishonest traffic towards their affiliate links in an attempt to fool careless users.
Naturally, this can severely hurt your site’s Search Engine Optimization (SEO). It could also negatively affect your bandwidth and storage, while making your site vulnerable to other security threats.
How to Spot If BabaYaga Has Infected Your Site
The BabaYaga white paper outlines a number of indicators of a compromised site. First of all, if your server is contacting the following host or IP, your site is most likely infected:
- 7od.info (178.132.0.105)
- my.wpssi.com (89.38.98.31)
You should also perform a Google search to see if your site is producing spam content. You can do this by going to Google and searching for site:https://yoursiteurlhere.com (obviously replacing the placeholder with your own site). If you find several pages you do not recognize that are clearly spam, you can be sure BabaYaga has affected your site:
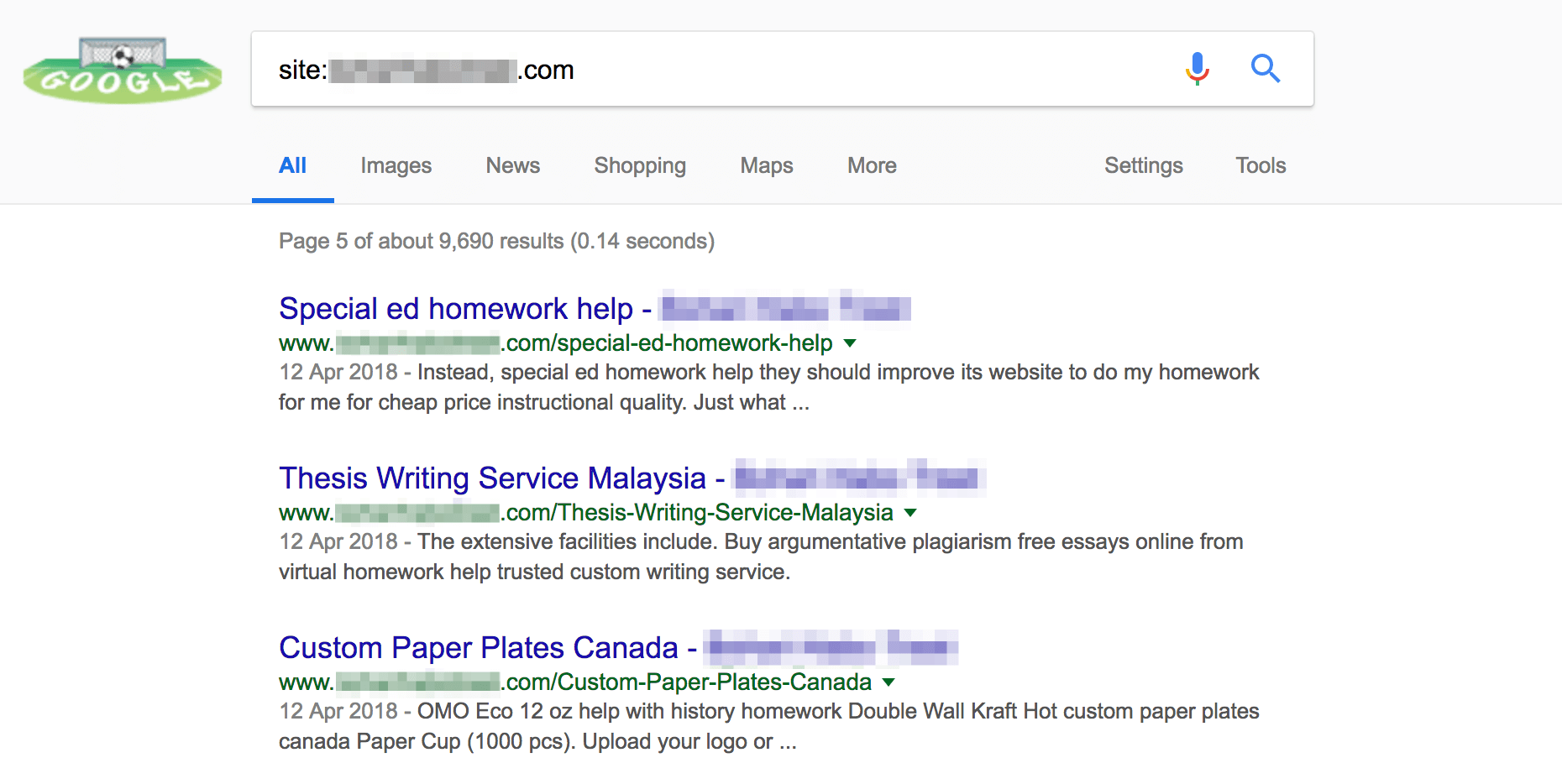
If you find that BabaYaga has got the worst of you, it’s time to clean up your site. You should start by running an anti-virus scan on your local machine, followed by changing all of your relevant passwords. This includes for your site, your File Transfer Protocol (FTP) credentials, and your server. You may also want to revert your site to a previous backup.
Because BabaYaga is unusually resilient, you may need to spend some time on scrubbing your site clean. You might even want to consider reaching out to Wordfence to help you clean your site if your efforts aren’t enough. We’ve recommended them before, and we don’t mind doing so again!
How to Protect Your Site From BabaYaga (And Other Malware)
If you’re fortunate in that your site hasn’t been infected by BabaYaga, this doesn’t mean you can relax just yet. In fact, your next step should be to ensure your site is protected. However, this doesn’t have to be a difficult process.
While BabaYaga is a particularly sly and difficult to detect malware, it’s still just malware. As such, you can deal with and stop it similarly to others. To prevent your site from being infected, you should make sure your site is secure in general.
We’ve discussed keeping your site secure before, so let us quickly recap some main points:
- Install a firewall and other security measures.
- Always use strong passwords and usernames for your WordPress site.
- Make sure your login screen is secure and stands up to brute force attacks.
- Scan your site for malware regularly.
- Keep WordPress, including your theme and plugins, updated at all times.
It’s also worth remembering that no security is perfect or everlasting. You need to keep up with new threats constantly, as attackers are always evolving their strategies. Even if you manage to stop BabaYaga at the door, there will always be new malware to follow tand be equally vigilant towards.
Conclusion
While WordPress is a secure platform at its core, there’s no shortage of malicious software trying to exploit it. The latest in line is BabaYaga, a type of malware that deletes other malware before infecting your site.
In this article, we’ve discussed the BabaYaga malware and how it can affect your WordPress site. We’ve also taken you through how to spot if this particularly elusive attacker has infected your site, and how you can get rid of it. Stay safe!
Source: Elegant Themes

